Meet the Scientists on the Frontlines of Protecting Humanity from a Man-Made Pathogen

From left: Jean Peccoud, Randall Murch, and Neeraj Rao.
Jean Peccoud wasn't expecting an email from the FBI. He definitely wasn't expecting the agency to invite him to a meeting. "My reaction was, 'What did I do wrong to be on the FBI watch list?'" he recalls.
You use those blueprints for white-hat research—which is, indeed, why the open blueprints exist—or you can do the same for a black-hat attack.
He didn't know what the feds could possibly want from him. "I was mostly scared at this point," he says. "I was deeply disturbed by the whole thing."
But he decided to go anyway, and when he traveled to San Francisco for the 2008 gathering, the reason for the e-vite became clear: The FBI was reaching out to researchers like him—scientists interested in synthetic biology—in anticipation of the potential nefarious uses of this technology. "The whole purpose of the meeting was, 'Let's start talking to each other before we actually need to talk to each other,'" says Peccoud, now a professor of chemical and biological engineering at Colorado State University. "'And let's make sure next time you get an email from the FBI, you don't freak out."
Synthetic biology—which Peccoud defines as "the application of engineering methods to biological systems"—holds great power, and with that (as always) comes great responsibility. When you can synthesize genetic material in a lab, you can create new ways of diagnosing and treating people, and even new food ingredients. But you can also "print" the genetic sequence of a virus or virulent bacterium.
And while it's not easy, it's also not as hard as it could be, in part because dangerous sequences have publicly available blueprints. You use those blueprints for white-hat research—which is, indeed, why the open blueprints exist—or you can do the same for a black-hat attack. You could synthesize a dangerous pathogen's code on purpose, or you could unwittingly do so because someone tampered with your digital instructions. Ordering synthetic genes for viral sequences, says Peccoud, would likely be more difficult today than it was a decade ago.
"There is more awareness of the industry, and they are taking this more seriously," he says. "There is no specific regulation, though."
Trying to lock down the interconnected machines that enable synthetic biology, secure its lab processes, and keep dangerous pathogens out of the hands of bad actors is part of a relatively new field: cyberbiosecurity, whose name Peccoud and colleagues introduced in a 2018 paper.
Biological threats feel especially acute right now, during the ongoing pandemic. COVID-19 is a natural pathogen -- not one engineered in a lab. But future outbreaks could start from a bug nature didn't build, if the wrong people get ahold of the right genetic sequences, and put them in the right sequence. Securing the equipment and processes that make synthetic biology possible -- so that doesn't happen -- is part of why the field of cyberbiosecurity was born.
The Origin Story
It is perhaps no coincidence that the FBI pinged Peccoud when it did: soon after a journalist ordered a sequence of smallpox DNA and wrote, for The Guardian, about how easy it was. "That was not good press for anybody," says Peccoud. Previously, in 2002, the Pentagon had funded SUNY Stonybrook researchers to try something similar: They ordered bits of polio DNA piecemeal and, over the course of three years, strung them together.
Although many years have passed since those early gotchas, the current patchwork of regulations still wouldn't necessarily prevent someone from pulling similar tricks now, and the technological systems that synthetic biology runs on are more intertwined — and so perhaps more hackable — than ever. Researchers like Peccoud are working to bring awareness to those potential problems, to promote accountability, and to provide early-detection tools that would catch the whiff of a rotten act before it became one.
Peccoud notes that if someone wants to get access to a specific pathogen, it is probably easier to collect it from the environment or take it from a biodefense lab than to whip it up synthetically. "However, people could use genetic databases to design a system that combines different genes in a way that would make them dangerous together without each of the components being dangerous on its own," he says. "This would be much more difficult to detect."
After his meeting with the FBI, Peccoud grew more interested in these sorts of security questions. So he was paying attention when, in 2010, the Department of Health and Human Services — now helping manage the response to COVID-19 — created guidance for how to screen synthetic biology orders, to make sure suppliers didn't accidentally send bad actors the sequences that make up bad genomes.
Guidance is nice, Peccoud thought, but it's just words. He wanted to turn those words into action: into a computer program. "I didn't know if it was something you can run on a desktop or if you need a supercomputer to run it," he says. So, one summer, he tasked a team of student researchers with poring over the sentences and turning them into scripts. "I let the FBI know," he says, having both learned his lesson and wanting to get in on the game.
Peccoud later joined forces with Randall Murch, a former FBI agent and current Virginia Tech professor, and a team of colleagues from both Virginia Tech and the University of Nebraska-Lincoln, on a prototype project for the Department of Defense. They went into a lab at the University of Nebraska at Lincoln and assessed all its cyberbio-vulnerabilities. The lab develops and produces prototype vaccines, therapeutics, and prophylactic components — exactly the kind of place that you always, and especially right now, want to keep secure.
"We were creating wiki of all these nasty things."
The team found dozens of Achilles' heels, and put them in a private report. Not long after that project, the two and their colleagues wrote the paper that first used the term "cyberbiosecurity." A second paper, led by Murch, came out five months later and provided a proposed definition and more comprehensive perspective on cyberbiosecurity. But although it's now a buzzword, it's the definition, not the jargon, that matters. "Frankly, I don't really care if they call it cyberbiosecurity," says Murch. Call it what you want: Just pay attention to its tenets.
A Database of Scary Sequences
Peccoud and Murch, of course, aren't the only ones working to screen sequences and secure devices. At the nonprofit Battelle Memorial Institute in Columbus, Ohio, for instance, scientists are working on solutions that balance the openness inherent to science and the closure that can stop bad stuff. "There's a challenge there that you want to enable research but you want to make sure that what people are ordering is safe," says the organization's Neeraj Rao.
Rao can't talk about the work Battelle does for the spy agency IARPA, the Intelligence Advanced Research Projects Activity, on a project called Fun GCAT, which aims to use computational tools to deep-screen gene-sequence orders to see if they pose a threat. It can, though, talk about a twin-type internal project: ThreatSEQ (pronounced, of course, "threat seek").
The project started when "a government customer" (as usual, no one will say which) asked Battelle to curate a list of dangerous toxins and pathogens, and their genetic sequences. The researchers even started tagging sequences according to their function — like whether a particular sequence is involved in a germ's virulence or toxicity. That helps if someone is trying to use synthetic biology not to gin up a yawn-inducing old bug but to engineer a totally new one. "How do you essentially predict what the function of a novel sequence is?" says Rao. You look at what other, similar bits of code do.
"We were creating wiki of all these nasty things," says Rao. As they were working, they realized that DNA manufacturers could potentially scan in sequences that people ordered, run them against the database, and see if anything scary matched up. Kind of like that plagiarism software your college professors used.
Battelle began offering their screening capability, as ThreatSEQ. When customers -- like, currently, Twist Bioscience -- throw their sequences in, and get a report back, the manufacturers make the final decision about whether to fulfill a flagged order — whether, in the analogy, to give an F for plagiarism. After all, legitimate researchers do legitimately need to have DNA from legitimately bad organisms.
"Maybe it's the CDC," says Rao. "If things check out, oftentimes [the manufacturers] will fulfill the order." If it's your aggrieved uncle seeking the virulent pathogen, maybe not. But ultimately, no one is stopping the manufacturers from doing so.
Beyond that kind of tampering, though, cyberbiosecurity also includes keeping a lockdown on the machines that make the genetic sequences. "Somebody now doesn't need physical access to infrastructure to tamper with it," says Rao. So it needs the same cyber protections as other internet-connected devices.
Scientists are also now using DNA to store data — encoding information in its bases, rather than into a hard drive. To download the data, you sequence the DNA and read it back into a computer. But if you think like a bad guy, you'd realize that a bad guy could then, for instance, insert a computer virus into the genetic code, and when the researcher went to nab her data, her desktop would crash or infect the others on the network.
Something like that actually happened in 2017 at the USENIX security symposium, an annual programming conference: Researchers from the University of Washington encoded malware into DNA, and when the gene sequencer assembled the DNA, it corrupted the sequencer's software, then the computer that controlled it.
"This vulnerability could be just the opening an adversary needs to compromise an organization's systems," Inspirion Biosciences' J. Craig Reed and Nicolas Dunaway wrote in a paper for Frontiers in Bioengineering and Biotechnology, included in an e-book that Murch edited called Mapping the Cyberbiosecurity Enterprise.
Where We Go From Here
So what to do about all this? That's hard to say, in part because we don't know how big a current problem any of it poses. As noted in Mapping the Cyberbiosecurity Enterprise, "Information about private sector infrastructure vulnerabilities or data breaches is protected from public release by the Protected Critical Infrastructure Information (PCII) Program," if the privateers share the information with the government. "Government sector vulnerabilities or data breaches," meanwhile, "are rarely shared with the public."
"What I think is encouraging right now is the fact that we're even having this discussion."
The regulations that could rein in problems aren't as robust as many would like them to be, and much good behavior is technically voluntary — although guidelines and best practices do exist from organizations like the International Gene Synthesis Consortium and the National Institute of Standards and Technology.
Rao thinks it would be smart if grant-giving agencies like the National Institutes of Health and the National Science Foundation required any scientists who took their money to work with manufacturing companies that screen sequences. But he also still thinks we're on our way to being ahead of the curve, in terms of preventing print-your-own bioproblems: "What I think is encouraging right now is the fact that we're even having this discussion," says Rao.
Peccoud, for his part, has worked to keep such conversations going, including by doing training for the FBI and planning a workshop for students in which they imagine and work to guard against the malicious use of their research. But actually, Peccoud believes that human error, flawed lab processes, and mislabeled samples might be bigger threats than the outside ones. "Way too often, I think that people think of security as, 'Oh, there is a bad guy going after me,' and the main thing you should be worried about is yourself and errors," he says.
Murch thinks we're only at the beginning of understanding where our weak points are, and how many times they've been bruised. Decreasing those contusions, though, won't just take more secure systems. "The answer won't be technical only," he says. It'll be social, political, policy-related, and economic — a cultural revolution all its own.
Kirstie Ennis, an Afghanistan veteran who survived a helicopter crash but lost a limb, pictured in May 2021 at Two Rivers Park in Colorado.
In June 2012, Kirstie Ennis was six months into her second deployment to Afghanistan and recently promoted to sergeant. The helicopter gunner and seven others were three hours into a routine mission of combat resupplies and troop transport when their CH-53D helicopter went down hard.
Miraculously, all eight people onboard survived, but Ennis' injuries were many and severe. She had a torn rotator cuff, torn labrum, crushed cervical discs, facial fractures, deep lacerations and traumatic brain injury. Despite a severely fractured ankle, doctors managed to save her foot, for a while at least.
In November 2015, after three years of constant pain and too many surgeries to count, Ennis relented. She elected to undergo a lower leg amputation but only after she completed the 1,000-mile, 72-day Walking with the Wounded journey across the UK.
On Veteran's Day of that year, on the other side of the country, orthopedic surgeon Cato Laurencin announced a moonshot challenge he was setting out to achieve on behalf of wounded warriors like Ennis: the Hartford Engineering A Limb (HEAL) Project.
Laurencin, who is a University of Connecticut professor of chemical, materials and biomedical engineering, teamed up with experts in tissue bioengineering and regenerative medicine from Harvard, Columbia, UC Irvine and SASTRA University in India. Laurencin and his colleagues at the Connecticut Convergence Institute for Translation in Regenerative Engineering made a bold commitment to regenerate an entire limb within 15 years – by the year 2030.

Dr. Cato Laurencin pictured in his office at UConn.
Photo Credit: UConn
Regenerative Engineering -- A Whole New Field
Limb regeneration in humans has been a medical and scientific fascination for decades, with little to show for the effort. However, Laurencin believes that if we are to reach the next level of 21st century medical advances, this puzzle must be solved.
An estimated 185,000 people undergo upper or lower limb amputation every year. Despite the significant advances in electromechanical prosthetics, these individuals still lack the ability to perform complex functions such as sensation for tactile input, normal gait and movement feedback. As far as Laurencin is concerned, the only clinical answer that makes sense is to regenerate a whole functional limb.
Laurencin feels other regeneration efforts were hampered by their siloed research methods with chemists, surgeons, engineers all working separately. Success, he argues, requires a paradigm shift to a trans-disciplinary approach that brings together cutting-edge technologies from disparate fields such as biology, material sciences, physical, chemical and engineering sciences.
As the only surgeon ever inducted into the academies of Science, Medicine and Innovation, Laurencin is uniquely suited for the challenge. He is regarded as the founder of Regenerative Engineering, defined as the convergence of advanced materials sciences, stem cell sciences, physics, developmental biology and clinical translation for the regeneration of complex tissues and organ systems.
But none of this is achievable without early clinician participation across scientific fields to develop new technologies and a deeper understanding of how to harness the body's innate regenerative capabilities. "When I perform a surgical procedure or something is torn or needs to be repaired, I count on the body being involved in regenerating tissue," he says. "So, understanding how the body works to regenerate itself and harnessing that ability is an important factor for the regeneration process."
The Birth of the Vision
Laurencin's passion for regeneration began when he was a sports medicine fellow at Cornell University Medical Center in the early 1990s. There he saw a significant number of injuries to the anterior cruciate ligament (ACL), the major ligament that stabilizes the knee. He believed he could develop a better way to address those injuries using biomaterials to regenerate the ligament. He sketched out a preliminary drawing on a napkin one night over dinner. He has spent the next 30 years regenerating tissues, including the patented L-C ligament.
As chair of Orthopaedic Surgery at the University of Virginia during the peak of the wars in Iraq and Afghanistan, Laurencin treated military personnel who survived because of improved helmets, body armor and battlefield medicine but were left with more devastating injuries, including traumatic brain injuries and limb loss.
"I was so honored to care for them and I so admired their steadfast courage that I became determined to do something big for them," says Laurencin.
When he tells people about his plans to regrow a limb, he gets a lot of eye rolls, which he finds amusing but not discouraging. Growing bone cells was relatively new when he was first focused on regenerating bone in 1987 at MIT; in 2007 he was well on his way to regenerating ligaments at UVA when many still doubted that ligaments could even be reconstructed. He and his team have already regenerated torn rotator cuff tendons and ACL ligaments using a nano-textured fabric seeded with stem cells.
Even as a finalist for the $4 million NIH Pioneer Award for high-risk/high-reward research, he faced a skeptical scientific audience in 2014. "They said, 'Well what do you plan to do?' I said 'I plan to regenerate a whole limb in people.' There was a lot of incredulousness. They stared at me and asked a lot of questions. About three days later, I received probably the best score I've ever gotten on an NIH grant."
In the Thick of the Science
Humans are born with regenerative abilities--two-year-olds have regrown fingertips--but lose that ability with age. Salamanders are the only vertebrates that can regenerate lost body parts as adults; axolotl, the rare Mexican salamander, can grow extra limbs.
The axolotl is important as a model organism because it is a four-footed vertebrate with a similar body plan to humans. Mapping the axolotl genome in 2018 enhanced scientists' genetic understanding of their evolution, development, and regeneration. Being easy to breed in captivity allowed the HEAL team to closely study these amphibians and discover a new cell type they believe may shed light on how to mimic the process in humans.
"Whenever limb regeneration takes place in the salamander, there is a huge amount of something called heparan sulfate around that area," explains Laurencin. "We thought, 'What if this heparan sulfate is the key ingredient to allowing regeneration to take place?' We found these groups of cells that were interspersed in tissues during the time of regeneration that seemed to have connections to each other that expressed this heparan sulfate."
Called GRID (Groups that are Regenerative, Interspersed and Dendritic), these cells were also recently discovered in mice. While GRID cells don't regenerate as well in mice as in salamanders, finding them in mammals was significant.
"If they're found in mice. we might be able to find these in humans in some form," Laurencin says. "We think maybe it will help us figure out regeneration or we can create cells that mimic what grid cells do and create an artificial grid cell."
What Comes Next?
Laurencin and his team have individually engineered and made every single tissue in the lower limb, including bone, cartilage, ligament, skin, nerve, blood vessels. Regenerating joints and joint tissue is the next big mile marker, which Laurencin sees as essential to regenerating a limb that functions and performs in the way he envisions.
"Using stem cells and amnion tissue, we can regenerate joints that are damaged, and have severe arthritis," he says. "We're making progress on all fronts, and making discoveries we believe are going to be helping people along the way."
That focus and advancement is vital to Ennis. After laboring over the decision to have her leg amputated below the knee, she contracted MRSA two weeks post-surgery. In less than a month, she went from a below-the-knee-amputee to a through-the-knee amputee to an above-the-knee amputee.
"A below-the-knee amputation is night-and-day from above-the-knee," she said. "You have to relearn everything. You're basically a toddler."

Kirstie Ennis pictured in July 2020.
Photo Credit: Ennis' Instagram
The clock is ticking on the timeline Laurencin set for himself. Nine years might seem like forever if you're doing time but it might appear fleeting when you're trying to create something that's never been done before. But Laurencin isn't worried. He's convinced time is on his side.
"Every week, I receive an email or a call from someone, maybe a mother whose child has lost a finger or I'm in communication with a disabled American veteran who wants to know how the progress is going. That energizes me to continue to work hard to try to create these sorts of solutions because we're talking about people and their lives."
He devotes about 60 hours a week to the project and the roughly 100 students, faculty and staff who make up the HEAL team at the Convergence Institute seem acutely aware of what's at stake and appear equally dedicated.
"We're in the thick of the science in terms of making this happen," says Laurencin. "We've moved from making the impossible possible to making the possible a reality. That's what science is all about."
7 Reasons Why We Should Not Need Boosters for COVID-19
A top infectious disease physician explains why immunity derived from natural infection and the vaccines should be long-lasting.
There are at least 7 reasons why immunity after vaccination or infection with COVID-19 should likely be long-lived. If durable, I do not think boosters will be necessary in the future, despite CEOs of pharmaceutical companies (who stand to profit from boosters) messaging that they may and readying such boosters. To explain these reasons, let's orient ourselves to the main components of the immune system.
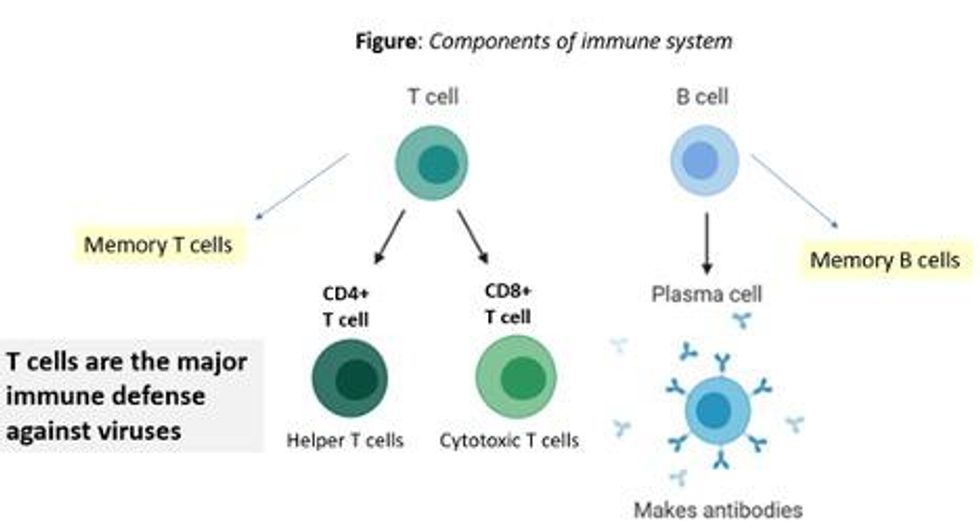
There are two major arms of the immune system: B cells (which produce antibodies) and T cells (which are formed specifically to attack and kill pathogens). T cells are divided into two types, CD4 cells ("helper" T cells) and CD8 cells ("cytotoxic" T cells).
Each arm, once stimulated by infection or vaccine, should hopefully make "memory" banks. So if the body sees the pathogen in the future, these defenses should come roaring back to attack the virus and protect you from getting sick. Plenty of research in COVID-19 indicates a likely long-lasting response to the vaccine or infection. Here are seven of the most compelling reasons:
REASON 1: Memory B Cells Are Produced By Vaccines and Natural Infection
In one study, 12 volunteers who had never had Covid-19--and were fully vaccinated with two Pfizer/BioNTech shots-- underwent biopsies of their lymph nodes. This is where memory B cells are stored in places called "germinal centers". The biopsies were performed three, four, six, and seven weeks after the first mRNA vaccine shot, and were stained to reveal that germinal center memory B cells in the lymph nodes increased in concentration over time.
Natural infection also generates memory B cells. Even after antibody levels wane over time, strong memory B cells were detected in the blood of individuals six and eight months after infection in different studies. Indeed, the half-lives of the memory B cells seen in the study examining patients 8 months after COVID-19 led the authors to conclude that "B cell memory to SARS-CoV-2 was robust and is likely long-lasting." Reason #2 tells us that memory B cells can be active for a very long time indeed.
REASON #2: Memory B Cells Can Produce Neutralizing Antibodies If They See Infection Again Decades Later
Demonstrated production of memory B cells after vaccination or natural infection with COVID-19 is so important because memory B cells, once generated, can be activated to produce high levels of neutralizing antibodies against the pathogen even if encountered many years after the initial exposure. In one amazing study (published in 2008), researchers isolated memory B cells against the 1918 flu strain from the blood of 32 individuals aged 91-101 years. These people had been born on or before 1915 and had survived that pandemic.
Their memory B cells, when exposed to the 1918 flu strain in a test tube, generated high levels of neutralizing antibodies against the virus -- antibodies that then protected mice from lethal infection with this deadly strain. The ability of memory B cells to produce complex antibody responses against an infection nine decades after exposure speaks to their durability.
REASON #3: Vaccines or Natural Infection Trigger Strong Memory T Cell Immunity
All of the trials of the major COVID-19 vaccine candidates measured strong T cell immunity following vaccination, most often assessed by measuring SARS-CoV-2 specific T cells in the phase I/II safety and immunogenicity studies. There are a number of studies that demonstrate the production of strong T cell immunity to COVID-19 after natural infection as well, even when the infection was mild or asymptomatic.
The same study that showed us robust memory B cell production 8 months after natural infection also demonstrated strong and sustained memory T cell production. In fact, the half-lives of the memory T cells in this cohort were long (~125-225 days for CD8+ and ~94-153 days for CD4+ T cells), comparable to the 123-day half-life observed for memory CD8+ T cells after yellow fever immunization (a vaccine usually given once over a lifetime).
A recent study of individuals recovered from COVID-19 show that the initial T cells generated by natural infection mature and differentiate over time into memory T cells that will be "put in the bank" for sustained periods.
REASON #4: T Cell Immunity Following Vaccinations for Other Infections Is Long-Lasting
Last year, we were fortunate to be able to measure how T cell immunity is generated by COVID-19 vaccines, which was not possible in earlier eras when vaccine trials were done for other infections (such as measles, mumps, rubella, pertussis, diphtheria). Antibodies are just the "tip of the iceberg" when assessing the response to vaccination, but were the only arm of the immune response that could be measured following vaccination in the past.
Measuring pathogen-specific T cell responses takes sophisticated technology. However, T cell responses, when assessed years after vaccination for other pathogens, has been shown to be long-lasting. For example, in one study of 56 volunteers who had undergone measles vaccination when they were much younger, strong CD8 and CD4 cell responses to vaccination could be detected up to 34 years later.
REASON #5: T Cell Immunity to Related Coronaviruses That Caused Severe Disease is Long-Lasting
SARS-CoV-2 is a coronavirus that causes severe disease, unlike coronaviruses that cause the common cold. Two other coronaviruses in the recent past caused severe disease, specifically Severely Acute Respiratory Distress Syndrome (SARS) in late 2002-2003 and Middle East Respiratory Syndrome (MERS) in 2011.
A study performed in 2020 demonstrated that the blood of 23 recovered SARS patients possess long-lasting memory T cells that were still reactive to SARS 17 years after the outbreak in 2003. Many scientists expect that T cell immunity to SARS-CoV-2 will be equally durable to that of its cousin.
REASON #6: T Cell Responses from Vaccination and Natural Infection With the Ancestral Strain of COVID-19 Are Robust Against Variants
Even though antibody responses from vaccination may be slightly lower against various COVID-19 variants of concern that have emerged in recent months, T cell immunity after vaccination has been shown to be unperturbed by mutations in the spike protein (in the variants). For instance, T cell responses after mRNA vaccines maintained strong activity against different variants (including P.1 Brazil variant, B.1.1.7 UK variant, B.1.351 South Africa variant and the CA.20.C California variant) in a recent study.
Another study showed that the vaccines generated robust T cell immunity that was unfazed by different variants, including B.1.351 and B.1.1.7. The CD4 and CD8 responses generated after natural infection are equally robust, showing activity against multiple "epitopes" (little segments) of the spike protein of the virus. For instance, CD8 cells responds to 52 epitopes and CD4 cells respond to 57 epitopes across the spike protein, so that a few mutations in the variants cannot knock out such a robust and in-breadth T cell response. Indeed, a recent paper showed that mRNA vaccines were 97.4 percent effective against severe COVID-19 disease in Qatar, even when the majority of circulating virus there was from variants of concern (B.1.351 and B.1.1.7).
REASON #7: Coronaviruses Don't Mutate Quickly Like Influenza, Which Requires Annual Booster Shots
Coronaviruses are RNA viruses, like influenza and HIV (which is actually a retrovirus), but do not mutate as quickly as either one. The reason that coronaviruses don't mutate very rapidly is that their replicating mechanism (polymerase) has a strong proofreading mechanism: If the virus mutates, it usually goes back and self-corrects. Mutations can arise with high rates of replication when transmission is very frequent -- as has been seen in recent months with the emergence of SARS-CoV-2 variants during surges. However, the COVID-19 virus will not be mutating like this when we tamp down transmission with mass vaccination.
In conclusion, I and many of my infectious disease colleagues expect the immunity from natural infection or vaccination to COVID-19 to be durable. Let's put discussion of boosters aside and work hard on global vaccine equity and distribution since the pandemic is not over until it is over for us all.

